|
The human factor.
You can't discuss computers without taking the human factor into account, and that's mostly what this page is about. All sorts of people use computers for all kinds of reasons; some consider it a necessary evil (filled with ritual pain), while others use the Mac to create and accomplish spectacular things. Some love these machines, others hate 'em.
What makes the difference? |


 You cannot be serious about security and run Windows.  If you look at maintenance time spent in the ongoing fight against malware, data theft, network threats and so-called "hackers" - virus scans, updates, quarantine and removal of countless Windows viruses on the loose - well, what if none o'that was necessary? What if all you really need is common sense? On the Mac, common sense should be enough to stop you from downloading and installing junk from the internet - if you're paying attention. Nothing gets installed without your participation and password. Fact is, most Mac users have never encountered a real virus.
That's not to say Mac users are immune to security issues. Threats include fake updates, fake virus warnings, phony viewers and PDF readers, nasty lil' browser extensions, fake cloud backup, and bogus utility apps that pretend to speedup, fixup or tuneup your Mac. Some of these scams involve credit card and bank accounts, others take you to a phony site hoping you'll enter your login for the real site, and some will appear to lock up your web browser with an "emergency" message and phone number to call for "help."
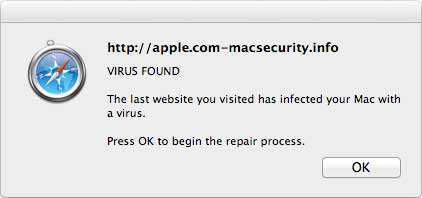 One of many phony virus warnings floating around the internet. This one launches FaceTime and activates your camera. The one thing all these scams have in common is the same thing that makes them harmless to savvy Mac users: They cannot get aboard without your participation. To that end, they try their very best to look convincing or pretend to be something useful. Don't call that number. Don't click that button. Don't download that crap. Here's a hint: If you avoid torrent sites, porn sites and shady web sites you'll avoid many of these scams. Malware, viruses, yada, yada... We've heard all about it, they make the news from time to time. Worms that destroy data, spyware, ransomware, adware, pop-ups and trojans, they infest the internet hoping to trick you into bringing them aboard. Once installed, they can redirect your browser, steal your info, record your keystrokes, spam all your friends, read your mail, turn your computer into a bot - or - just screw things up and call it a day.
If you simply IGNORE the junk that comes your way uninvited, you'll be fine. That said, there's nothing to prevent you from downloading and installing some sort of internet trash, but you'll have to enter your admin password to do it. Just don't go there. Don't download. Don't install. Don't enter your password. Stay focused and ignore all the flak that passes by online. If you need something, go to the legitimate source and get it. If it comes looking for you, you don't want it. Pay attention!
Another annoying scam - courtesy of Google - is phony customer support. Search Google for "[company name] customer support" and you'll find yourself looking at a very convincing toll-free phone number. If you're foolish enough to call that number, you'll find a "technician" on the other end who is happy to help you, just as soon as you download a remote access app (GoToMeeting, LogMein, Teamviewer, GoToMyPC, to name a few). No matter which app is used, installing it gives the thieves full access to all data on your machine - so DON'T GO THERE.
Remote access programs serve a legitimate purpose when they're in the right hands, so it's all about knowing - and trusting - the people you are dealing with. If you called a real phone number for Apple or Canon or HP or some other legitimate company - a number provided by the actual company - you have little to worry about. But, if the number you called came from a top Google hit or pop-up, you're doomed. If you gave remote access to a scammer, your next move should be to cancel your credit card, notify your bank, and change ALL of your passwords ASAP. Hopefully you can do all that before you become another victim. Which brings us to a relatively new phenomenon known as ransomware. In the Mac world, this includes a handful of utility apps which may actually serve a purpose with a well-designed interface, but the _real_ purpose is to wring money out of you. They may be free downloads or might be purchased. They can arrive in unscrupulous ways from unscrupulous sources, do their thing from a free demo or come piggybacked on a torrent download. Once installed they can be difficult to remove; even after deleting the app, ransomware will leave files behind that cause trouble.
MacKeeper is a prime example. Promising to speed up your Mac, it has a nice interface with a lot of unnecessary and redundant functions. But, if you delete MacKeeper, it leaves hidden files behind that will slow your Mac to a crawl and leave you staring at beachballs - the very problem it pretends to solve - in the hopes you'll buy it. And if you do, you don't dare delete it or stop buying "updates." You're hostage to it. For the record, the more serious forms of ransomware are designed to lock up servers and prevent access to a company's own database until a ransom is paid, typically in bitcoin. To date, the Apple platform has suffered exactly one of these, related to an app for downloading from torrent sites. We've been warning about torrent sites for years and have little sympathy for those who use such sites. Clean out the cruft and keep up your guard
Most browsers have privacy and/or security controls in the browser's preferences where you can view and delete cookies. Watch for "evercookies" (these return moments after being deleted). Reset your browser regularly, avoid browser extensions, and pay attention to unusual activity. (See cleanup ops here.)
Research any apps or utilities you may be interested in before you download and/or install such things (including free demos). Avoid torrent, "sharing" and suspect web sites. Delete suspicious emails immediately, never click on (phishing) links they may contain or reply with personal info. Don't let other people mess with your machine; if you share a computer with others, you should each have your own login accounts and passwords. Anyone borrowing your Mac temporarily should use the Guest account.
Apple makes its Operating System as fast and trouble-free as possible; there are no third-party apps that can improve operation or speed. Running Apple's Disk Utility > First Aid periodically to verify your drive is the only routine maintenance needed. With a little common sense you can easily avoid a good deal of trouble and grief. Also see nCity's "Security and Protection" page (left sidebar) if you're interested. Pay close attention to search results when looking for assistance or software. We're getting clients who have gone looking for online help with printers, apps or other things, only to be fooled into installing a remote access program allowing scammers to copy whatever they want.
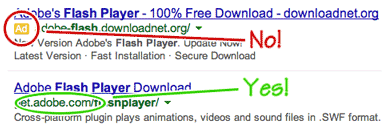 Examine actual site addresses, ignore pop-ups and ads, don't give out info, and avoid scam sites that want to draw you in. Do a little research before you download anything. |

 Why it may be best to stay a version - or two - behind  An example of what can happen when upgrades are rushed to release It's important to understand the difference between updates and upgrades: An update is an improvement to your existing OS version - a bug fix, new feature or security enhancement - but an upgrade means replacing the entire OS with a newer one. Updates are almost always desirable. Upgrades, on the other hand, may cause a fair amount of disruption, especially if you are jumping over multiple OS versions. Release of Catalina 10.15 in late-2019 marked some major changes: It was the last Intel-native OS, last of OSX-series Systems, the first OS to require a solid-state drive (SSD), and first to have OS on a locked partition. It also ended support for 32-bit apps. Catalina is the last OS for most 2012 Macs, except a few late-2012 models that end on OS 11 Big Sur.
OS 11 Big Sur (late 2020) was the first System designed for Apple's new M-series processors, replacing 20 years of Intel CPUs. Switching processors affects most everything downstream; hardware, ports, OS, security and software - which is no small matter. Then came OS 12 Monterey, OS 13 Ventura, OS 14 Sonoma, etc. With each new OS, Apple drops support for an old one, and older Macs face obsolescence.
It's worth noting that you will be prevented from downloading or installing incompatible upgrades. Past OS upgrades are still available, many are posted on our All Things Apple page. "Full backup" is more than just drag/drop copies or cloud backup; it means making a full and complete copy of your machine's drive to a second volume, a second (backup) drive. This is the only way to leave yourself an "undo" option if an install or upgrade goes wrong. You should maintain a full, current and complete backup to an external drive in any case, but _always_ backup all data prior to making any major change. If you don't have a backup drive, get one! Cloud doesn't cut it.
Check system requirements
Each Operating System has specific processor, machine and memory requirements that will prevent installation if your Mac doesn't qualify.
Links to Apple OS/machine specs:
Long-term suggestion:Know your current Operating System and keep it current with updates as they become available. Before you upgrade to a newer OS version, check for compatibility of key apps with the new OS, but don't upgrade without a compelling reason. Recommend turning OFF auto-update. In short: If it works, don't fix it.
|


 Might be time to drop a dime. If this is the Information Age, it's being driven by the Internet and we each need to grab hold of those handlebars and pay attention. The web can be the ultimate research tool, but like any tool it may be used in a variety of ways, even as a weapon. As you read this, fights are raging over controlling access and content, with tax revenue and censorship in mind. It's a fragile thing to be won or lost, and minor changes can have drastic effects. This subject, like most anything else you might be interested in, can (still) be investigated on the Web using a variety of search engines - besides Google or Yahoo.
Using information technology has become mandatory, like being able to read and write. We each must develop our skills at dealing with search criteria and technique in order to be proficient. Why? Because it is important to know what - and who - you're dealing with today.
Spying is for no-goodniks? If you still respect privacy and decency, and you think "spying" is beneath you, please think again. You really do need to take those blinders off in cyberspace if you want a fighting chance, and don't wait until it's too late. Do it immediately, before making any decisions or commitments, before clicking that send button, make investigation a part of your routine. It's not about spying or being rude, it's about staying on top of changing circumstances and making informed decisions.
Why bother...
If you (more correctly) consider online research to be a valuable tool and useful asset, but not necessarily appropriate in social circles - I sympathize, but can no longer agree. Personally, I believe those sentiments belong in the past now, along with so many other matters of civility and common sense these days. In some quarters, it's every man for himself. So call it spying if you like - or researching or investigating or shopping or sleuthing or advertising or promoting or networking - as these terms all do apply. But also consider it prudent and necessary in the modern world. And while you're at it, you might consider investigating yourself to see what others will find out from researching you. It's easier than you might think. If you're on Facebook, you've thrown open all doors and windows and joined the party, so you might as well start there. But, as research tools go, social sites lack validation and we only want facts here. I recommend skipping right past Fbook and other sites of that ilk in favor of drilling much deeper for official records, detailed stats, and facts from reliable sources.
The Internet may be the ultimate "killer app" of the computer world, long as regulation and greed doesn't throttle it back. You should know, and be aware, that many forces are at work trying to control your access and redirect your attention (see Electronic Frontier Foundation for the latest), so you must stay focused and be determined to get at the truth. It helps to be resourceful as well. Your degree of difficulty will vary depending on what type of info you seek and how sensitive that info might be. Here are three broad categories:
Every private eye on the planet keeps a variety of go-to web sites and sources for searching out answers and locating info, and so should you. Create a folder for search sites in the bookmarks menu of your browser (Safari, Firefox, Etc.) and start collecting sites that serve your purposes best. We can help you sort thru countless resources available on the web and suggest a few ways to obtain factual data you may be unaware of, but be advised that some of these services charge fees and you don't always get what you pay for. You should also be prepared for the possibility of bad news or learning _more_ than you might have wanted to know. "Trust but verify." A word of caution here: It's always best to confirm findings with a secondary, independent source before jumping to conclusions.
|

|
We've used Macs to remodel houses, design and build furniture and mechanical devices, make motorcycle modifications, create artwork, design databases and produce printed circuits. Edit and store audio/video, photographs and graphics, text and data. Plus, Macs keep the books, manage communications and provide endless material for research purposes and entertainment. I mention this because there are still people out there who wonder what they'd ever do with a computer. Hello?
The first "killer application" was word processing.
The ability to type and edit a document _before_ printing was reason enough to buy a computer, just to replace that old typewriter. Today, most folks recognize internet access as being a whole new window on the world, with email and texting as the new means of communications, all of which are excellent reasons to invest in a computer. (Even if all you use a computer for is email and web, using a Mac provides a big advantage due to security features and ease of use.) But there is so much more you can do, it seems like a waste of power to stop at communications without branching off into other things.
Your Mac comes equipped with software designed to manage a great many basic necessities, beyond communications; photos, text, music, address books, tax prep, all sorts of things. It even comes with a set of developer tools for creating your own programs, and all the basics are covered right out of the box. For specialized applications, you'll find all kinds of additional hardware and software available for most any use these days. Our Link pages contain a wide variety of recommended products and vendors; there's also a link to Apple's index of Mac apps where you'll find thousands of programs designed to do almost anything you can think of.
One odd thing about software:
Good programs always seem deceptively simple, with a tasteful, coherent interface, easy to use and understand - which tends to conceal the program's true power. If you can accomplish a given task with one click, it's because the program's designer has dealt with all the details for you. If you have to wade through an assortment of buttons and dialog boxes to accomplish that same task, then the programmer has decided to let you do all the work - easy for them, not so easy for you. And somehow, bad software seems to leave an impression of "sophistication" due to the complexity of dealing with it.
It pays to shop around and test drive applications before buying. The cumulative effect of using bad software can translate into a considerable waste of time and repetitive effort, which will more than offset any money saved in its purchase price. (Also true of Operating Systems and hardware, by the way.) Having said that, you may find you already have a program capable of assisting with whatever project you have in mind and additional software won't be necessary. I've often used simple graphics apps for remodel projects and precision design work, everything from MacPaint to Photoshop.
Be creative! Apply the power of your Mac to whatever holds your interest. You might find an app onboard that can handle your project, or you might decide to invest in specialized software to accomplish something amazing. Just, p-p-please don't look at the Mac as an ordinary computer or some sort of appliance. Explore just a few of the things it can do and you'll be amazed.
|